1. swoole
题目链接:
Make unserialize great again
https://swoole.rctf2020.rois.io
hint:https://github.com/swoole/library/issues/34
参考资料:
#!/usr/bin/env php
<?php
Swoole\Runtime::enableCoroutine($flags = SWOOLE_HOOK_ALL);
$http = new Swoole\Http\Server("0.0.0.0", 9501);
$http->on("request",
function (Swoole\Http\Request $request, Swoole\Http\Response $response) {
Swoole\Runtime::enableCoroutine();
$response->header('Content-Type', 'text/plain');
// $response->sendfile('/flag');
if (isset($request->get['phpinfo'])) {
// Prevent racing condition
// ob_start();phpinfo();
// return $response->end(ob_get_clean());
return $response->sendfile('phpinfo.txt');
}
if (isset($request->get['code'])) {
try {
$code = $request->get['code'];
if (!preg_match('/\x00/', $code)) {
$a = unserialize($code);
$a();
$a = null;
}
} catch (\Throwable $e) {
var_dump($code);
var_dump($e->getMessage());
// do nothing
}
return $response->end('Done');
}
$response->sendfile(__FILE__);
}
);
$http->start();
2. rBlog 2020
题目链接:
https://rblog.rctf2020.rois.io
The source deployed on the server has been slightly modified to ensure the isolation of every single payload.
hint:https://developer.mozilla.org/en-US/docs/Web/JavaScript/Reference/Global_Objects/String/replace
3. chowder_cross
题目链接:
try to bypass chowder filter to get flag
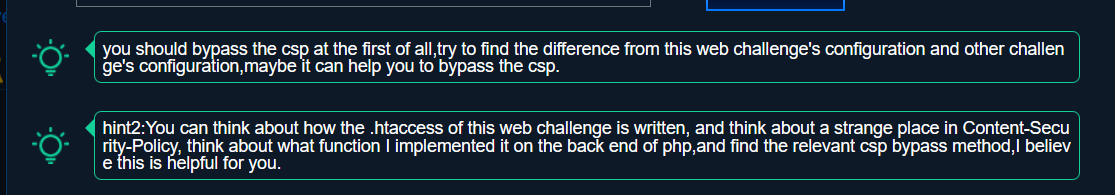
hint3: Try to visit the non-existent page and see what happens, pay attention to img-src to see what happens, please combine my previous hints.
4. Calc
题目链接:
nobody knows php better than me, So calc it
http://124.156.140.90:8081
5. EasyBlog
come and write something
http://124.156.134.92:8081